VLAN
What is VLAN?
The full name of VLAN is Virtual Local Area Network. VLAN technology can divide the physical LAN port on the device into multiple broadcast domains, and each VLAN is a broadcast domain. VLAN can be defined, and up to 4094 VLANs can be defined. Different VLANs have different VLAN tags. Devices in the same VLAN can communicate with each other, but VLANs in different VLANs cannot communicate directly with each other.
Why Do We Need VLAN?
In the early days of Ethernet technology, the network used a data network communication logical division similar to the broadcast domain. When there are a large number of devices, it will cause serious data conflicts and network congestion. You can imagine this, assuming that you need to send a sale volume document to the finance department, but the company's local area network uses broadcast domain technology, all hosts in the local area network will receive it every time you send a file. Because the broadcast domain can’t isolate internal devices, you will also receive files sent by other colleagues that are not related to you while you are working, which causes a huge waste of network resources and inefficient office work.
To solve this problem, you invented the STP spanning tree technology, which allows calculations to be performed on each message to ensure that there is only one optimal active path for the message to any destination. However, this also brings problems. The more devices there are, the higher the cost of calculating the path, which limits the scale of the network and also causes the network to converge very slowly.
With VLAN technology, you can create a separate VLAN for each department's host, and each time you send a file to the broadcast domain, it will not be sent to other hosts outside the domain. And you can create hosts for 4094 departments, so you don't have to worry about it for the time being.
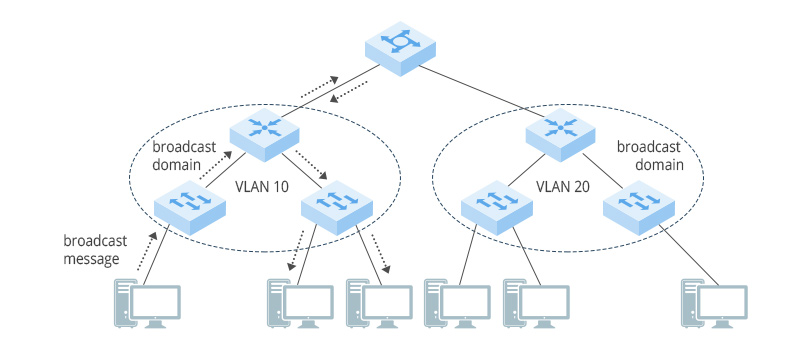
How Does VLAN Function?
Users in the same VLAN may be connected to different switches, and there may be multiple VLANs in this case. As mentioned before, VLANs are tagged for easy identification. However, some devices such as computers can only process data without VLAN tags. The switch port needs to process the data transmission and reception differently depending on the connection object, so VLAN has multiple port types.
Taking Cisco devices as an example, common port types are Access and Trunk ports.
Access Port
Access ports are generally used to connect to devices that cannot identify VLAN tags, such as PCs, or when there is no need to distinguish data frames between different VLANs. When the access port sends and receives untagged frames, the switch only processes data frames with VLAN tags. Therefore, the access port needs to add VLAN tags to the received data frames. To add VLAN tags, the PVID (Port Default VLAN ID) must be configured.When the access port receives a frame with a tag and the VID in the frame is the same as the VID (PVID) of the port, the access port can also receive and process the frame.If the VID in the received tagged data frame is different from the port's VID, the access will not process the data in the frame and will directly discard it.
Before sending a tagged frame, the access port will strip off the tag. The reason for this is that devices such as hosts or servers cannot process tagged VLANs.
Trunk Port
Trunk ports are generally used to connect switches, routers, and other devices that can send and receive tagged and untagged frames at the same time. When a Trunk port receives an untagged frame, it adds a tag corresponding to the PVID to the untagged frame.When a Trunk port receives a tagged data frame, it does not make any changes. A Trunk port can be configured with a list of multiple VLANs. But one thing needs to be mentioned: data frames that only allow PVID to be sent from the TRUNK port are not tagged.
Application of VLAN
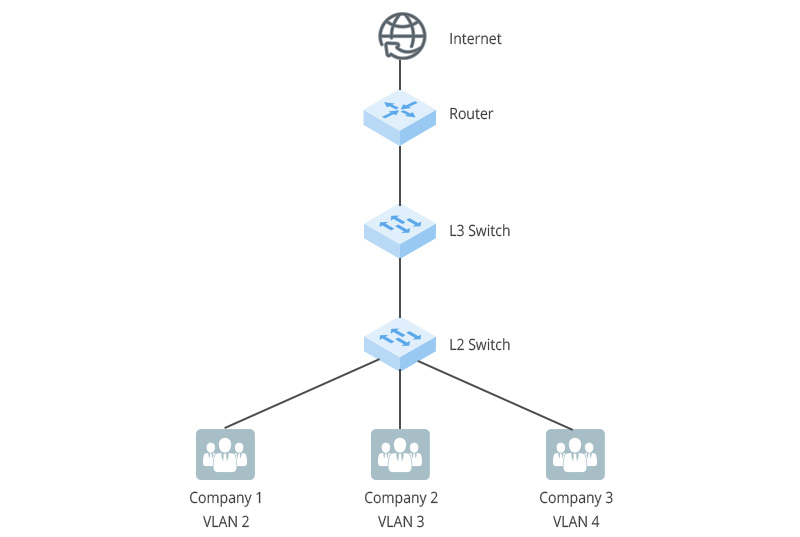
Case 1: Port-based division
It is common that there are multiple companies in a building, and these companies are connected to the same Layer 2 switch. In order to ensure the independence and security of each company's business, the interface connected to each company can be divided into different VLANs to achieve complete isolation of business data between companies.
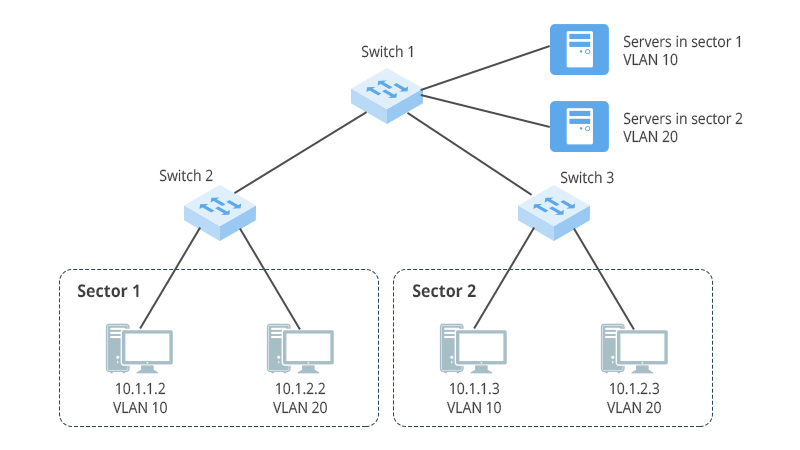
Case 2: Division based on IP network segment
The company has multiple departments, and the hosts of each department are configured with different network segments. The company hopes that the network resources accessed by employees in each department are isolated from each other. VLAN division based on IP subnet can be configured on the company's switch Switch_1. In this way, different network segments of the server are divided into different VLANs, and the data flows accessing different application services of the server will be isolated, which improves security.