WPA3
WPA3 (Wi-Fi Protected Access 3) is a next-generation Wi-Fi encryption protocol released by the Wi-Fi Alliance organization in 2018, which improves WPA2 by adding many new features to provide more robust encryption protection for data transmission between users and Wi-Fi networks. Depending on the use and security needs of Wi-Fi networks, WPA3 is categorized into WPA3-Personal, WPA3-Enterprise, and OWE certification for open Wi-Fi networks.
Features and Benefits of WPA3
Stronger Data Encryption
WPA3 uses a personalized data encryption mechanism that provides a unique encryption key for each data transmission. Compared to WPA2, WPA3 has a longer encryption key, using a 192-bit key for personal mode and a 256-bit key for enterprise mode, significantly enhancing data security and privacy.
SAE
The SAE protocol uses stronger encryption algorithms and more secure key exchange methods, effectively preventing offline attacks and password-guessing attempts, and improving network security.
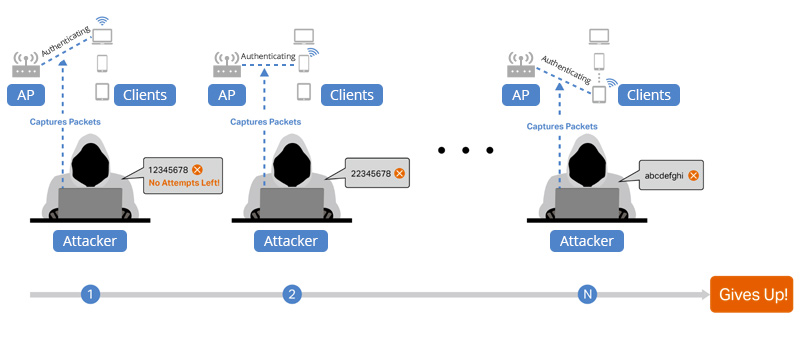
Improved Brute Force Attack Protection
WPA3 features improved brute force attack protection to protect users from dictionary attacks and brute force decryption effectively. By limiting the number of attempts and using more complex encryption keys, WPA3 prevents hackers from brute-force breaking Wi-Fi passwords and credentials.
Enterprise-level Security Protection
WPA3 Enterprise Edition further improves the security based on WPA2 Enterprise Edition by introducing WPA3-Enterprise 192bit mode with 192-bit Suite-B security suite, which enhances the strength of password defence. Meanwhile, WPA3-Enterprise adopts the more secure HMAC-SHA-384 algorithm for key export and confirmation, strengthening data protection.
Open Network Protection
WPA3 introduces an enhanced open network authentication method, OWE (Opportunistic Wireless Encryption), which provides more secure protection for user data transmission over open networks. OWE uses the Diffie-Hellman key exchange algorithm for key exchange and encrypts user data transmission, effectively preventing illegal access and data theft by attackers.
Disadvantages of WPA3
Dragonfly Handshake Vulnerability: WPA3 introduced the Dragonfly handshake protocol to protect against offline dictionary attacks, but researchers have discovered a vulnerability in the Dragonfly handshake process that could allow an attacker to perform a bypass attack to obtain information about the password used. This vulnerability makes WPA3 security challenging.
Downgrade Attacks: Although WPA3 is designed to be more secure, networks often support both WPA2 and WPA3 standards due to backward compatibility concerns. Attackers can take advantage of this by forcing devices to downgrade to connect using the less secure WPA2 protocol, thereby bypassing the security enhancements of WPA3.
Implementation Flaws: The security of WPA3 also depends on how it is implemented. Some early implementations of WPA3 had flaws, particularly in the implementation of the Dragonfly handshake, which was vulnerable to various attacks. These issues could lead to attackers bypassing WPA3 security mechanisms, thereby jeopardizing network security.
Limited Adoption and Compatibility Issues: WPA3 security improvements are limited by its adoption rate and compatibility issues. Many devices are still using older Wi-Fi security protocols due to hardware limitations or lack of firmware updates. This limited adoption means that many networks need to be more vulnerable to the very attacks that WPA3 is designed to mitigate, limiting the practical effectiveness of WPA3.
Is it Necessary to Upgrade to WPA3?
The security of WPA3 is much higher than that of WPA2, and it is recommended that WPA3 be used to protect the Wi-Fi network if the actual conditions are met. However, the transition from WPA2 to WPA3 is gradual, and you may face a transition period caused by equipment updates or software updates. Before switching to WPA3, you can use updated security patches and increase the password complexity to improve the security of your current Wi-Fi network.












