Comparing Wi-Fi Security Types: WEP vs. WPA vs. WPA2 vs. WPA3
Wi-Fi security protects our privacy and data from unauthorized access and eavesdropping. The terms WEP, WPA, WPA2 and WPA3 come up frequently when using wireless products such as APs and routers, but what is the difference between WEP vs. WPA vs. WPA2 vs. WPA3? This article explains the differences between these four Wi-Fi security protocols to help readers better understand and secure their networks.
What is WEP?
Wired Equivalent Privacy Definition
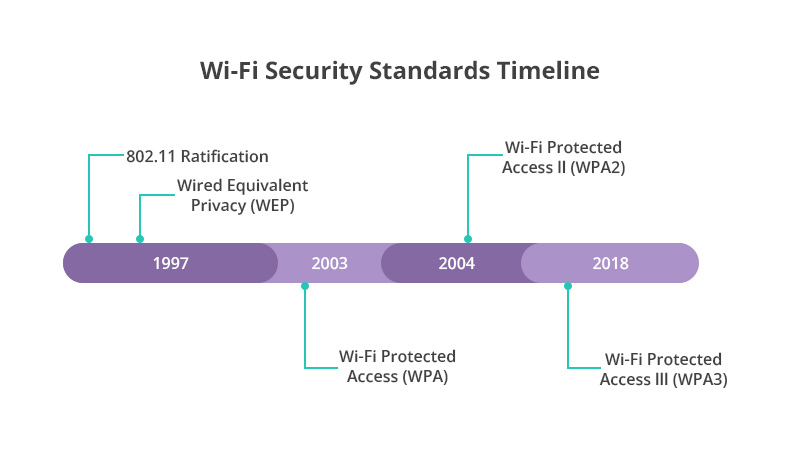
Short for Wired Equivalent Privacy, WEP was first introduced in 1997 as a way to encrypt data transmitted wirelessly between two devices to prevent unauthorized users from eavesdropping on or intruding into a wireless network. The working principle of WEP is to use encryption algorithms to encrypt data transmitted over the wireless network. It uses 64-bit and 128-bit keys to encrypt data and uses these keys to authenticate and decrypt data packets. At that time, Wi-Fi technology was still in its infancy, and people were beginning to realize the need for a security protocol to prevent unauthorized access and eavesdropping. WEP is considered a milestone because it was the first standard to provide security for Wi-Fi networks.
Drawbacks to WEP Security
One of the most significant disadvantages of WEP is that the keys are vulnerable to attack. Because WEP uses static keys and has weaknesses in its encryption algorithm, hackers can use simple tools and techniques to crack WEP encryption and access protected Wi-Fi networks easily.
In addition, WEP also has vulnerabilities, such as replay attacks and dictionary attacks, which threaten network security.
What is WPA?
Wi-Fi Protected Access Definition
Wi-Fi Protected Access (WPA) was introduced in 2003 as a direct response and replacement to the Wi-Fi Alliance's increasingly apparent vulnerabilities in the WEP encryption standard. WEP was one of the earliest encryption standards adopted by Wi-Fi networks, but its static keys and vulnerable encryption algorithms made network data vulnerable to theft and tampering. The advent of WPA filled the security holes of WEP and provided more reliable protection for wireless networks.
Improvements over WEP Security Protocol
Temporal Key Authority Protocol (TKIP): WPA uses the TKIP protocol to generate a new key for each transmitted packet. Unlike WEP, which uses the same static key, TKIP reduces the attacker's available information by regularly changing the key, making it more difficult to hijack packets.
Message Permission check (MIC): WPA includes a message permission check to see if an interceptor has intercepted and changed the data packet. This feature helps prevent attacks and data tampering.
What is WPA2?
Wi-Fi Protected Access 2 Definition
WPA2 is an upgraded version of the WPA protocol. It was launched in 2004 to provide more secure wireless network connections. WPA2 secures Wi-Fi networks through encryption and authentication mechanisms. When a device connects to a protected Wi-Fi network, it is first authenticated to ensure only authorized users can access it. Subsequently, the data is encrypted using the AES encryption algorithm to ensure data security during transmission. At the same time, WPA2 also uses the counter mode of the Cipher Block Chain Message Verification Code Protocol (CCMP) to verify the integrity of the data and prevent the data from being tampered with or damaged.
Improvements over WPA Security Protocol
Strong encryption: WPA2 uses the Advanced Encryption Standard (AES), which is more secure and reliable than the early WEP and TKIP encryption algorithms. The AES algorithm uses a 128-bit or 256-bit key length, providing higher encryption protection and effectively preventing various attacks on Wi-Fi networks.
Robust authentication: WPA2 supports two authentication modes: WPA2-Personal and WPA2-Enterprise. In individual mode, a pre-shared key (PSK) is usually used, i.e., the password for the Wi-Fi network is shared between the access point and the connected device. Enterprise mode uses the more complex Extensible Authentication Protocol (EAP) to provide individual credentials for each user or device through a separate authentication server.
What is WPA3?
Wi-Fi Protected Access 3 Definition
WPA3 is the latest Wi-Fi security protocol released by the Wi-Fi Alliance in 2018. As the successor to WPA2, WPA3 is designed to provide more robust security protections, address some of the security vulnerabilities and attack tactics in WPA2, and provide a more secure Wi-Fi connection for personal and business users.
Improvements over WPA 2 Security Protocol
Stronger Data Encryption
WPA3 uses a personalized data encryption mechanism that provides a unique encryption key for each data transmission. Compared to WPA2, WPA3 has longer encryption keys, using a 192-bit key for personal mode and a 256-bit key for enterprise mode, significantly enhancing data security and privacy.
Higher Network Security
In WPA3, the AES encryption algorithm is implemented through the SAE protocol, which employs more robust encryption algorithms and more secure essential exchange methods, effectively preventing offline attacks and password-guessing attempts and improving network security.
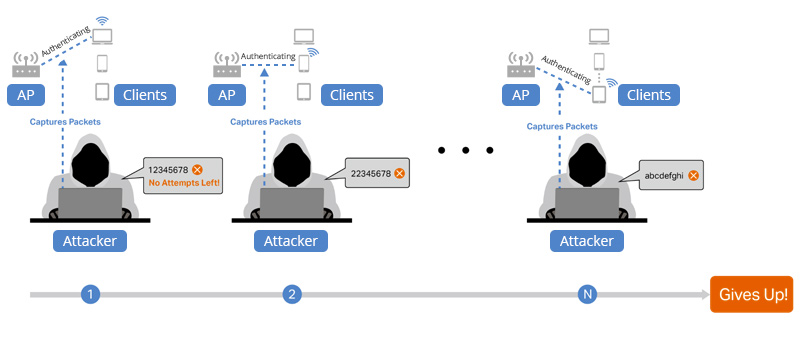
Improved Brute Force Attack Protection
WPA3 features improved brute-force attack protection, protecting users from dictionary attacks and brute-force cracking. By limiting the number of attempts and using more complex encryption keys, WPA3 prevents hackers from brute-force breaking Wi-Fi passwords and credentials.
Enterprise-grade Security Protection
WPA3-Enterprise further improves security based on WPA2-Enterprise by introducing the WPA3-Enterprise 192-bit mode, improving password defense strength. Meanwhile, WPA3-Enterprise adopts the more secure HMAC-SHA-384 algorithm for key export and confirmation, strengthening data protection.
Open Network Protection
WPA3 introduces OWE (Opportunistic Wireless Encryption), which provides more secure protection for user data transmission over open networks. OWE uses the Diffie-Hellman key exchange algorithm for key exchange and encrypts user data transmission, effectively preventing illegal attackers from accessing and stealing data.
Do You Need WPA3 Wi-Fi Security Type?
The security of WPA3 is much greater than that of WPA2, and it is recommended to use WPA3 to protect the Wi-Fi network if the actual conditions are met. However, the transition from WPA2 to WPA3 is gradual, and you may face a transition period caused by equipment updates or software updates. Before switching to WPA3, you can use updated security patches, increase password complexity, etc., to improve the security of the current Wi-Fi network.
WEP vs. WPA vs. WPA2 vs. WPA3 Network Wireless Security, What are the Differences?
The differences between WEP vs. WPA vs. WPA2 vs. WPA3 are shown in the table below.
How to Choose the Right Wireless Network Security Protocols?
WEP is an outdated Wi-Fi security protocol and should be avoided. WPA is an alternative to WEP and uses more robust encryption. Currently, WPA2 is the dominant wireless security protocol. Most current devices, including smartphones, laptops, and wireless access points, have built-in support for WPA2. Although WPA3 is the most advanced security protocol, it is not yet as popular as WPA2 due to compatibility issues.
Therefore, it is recommended that you choose the proper Wi-Fi security protocol in this order.
Preferred: If possible, choose WPA3, which provides the highest level of security.
Second Best Choice: If WPA3 is not supported, WPA2 is the most secure and widely supported choice.
Avoid using WEP and WPA unless there is no other choice, and only for networks that do not involve sensitive data.
Conclusion
Wi-Fi security has improved from WEP to WPA3, with each generation of protocols improving encryption technology and security. WEP was the first security protocol, but WPA replaced it because it was easy to crack. WPA improved network security by introducing dynamic key management and stronger encryption. WPA2 further strengthened encryption and became a widely used standard today, while WPA3 builds on this foundation by providing more advanced security features and protection mechanisms.












